State of Industrial Control Systems (ICS) in Italy
Table of Contents
Industrial Control System, what are they?
TL;DR: In a nutshell, Industrial control systems (ICS) are “computers” (PLC) that control the world around you. They’re responsible for managing the air conditioning in your office, the turbines at a power plant, the lighting at the theatre or the robots at a factory
Industrial Control System (ICS) is a general term used to describe several types of control systems and associated instrumentation used for industrial process control.
Such systems can range from a few modular panel-mounted controllers to large interconnected and interactive distributed control systems with many thousands of field connections. ICS receive data from remote sensors measuring process variables (PVs), compare these with desired set points (SPs) and derive command functions which are used to control a process through the final control elements (FCEs), such as control valves.
The larger systems are usually implemented by Supervisory Control and Data Acquisition (SCADA) systems, or distributed control systems (DCS), and programmable logic controllers (PLCs).
Such systems are extensively used in industries such as chemical processing, pulp and paper manufacture, power generation, oil and gas processing and telecommunications.
For those who are not familiar with this terminology, at the end of the article I have included a glossary of terms and common acronyms.
ICS & SCADA High Level diagram

SCADA/ICS Cyberattacks
Stuxnet: a malware, first uncovered in 2010. Stuxnet targets SCADA systems and is believed to be responsible for causing substantial damage to Iran’s nuclear program. Stuxnet specifically targets programmable logic controllers (PLCs), such as those used to control industrial processes including centrifuges for separating nuclear material. Stuxnet reportedly compromised Iranian PLCs, causing the fast-spinning centrifuges to tear themselves apart. Stuxnet reportedly ruined almost one fifth of Iran’s nuclear centrifuges.
Crash Override/ Industroyer: a malware considered to have been used in the cyberattack on Ukraine’s power grid on December 17, 2016. The attack cut a fifth of Kiev, the capital, off power for one hour and is considered to have been a large-scale test. The Kiev incident was the second cyberattack on Ukraine’s power grid in two years. The first attack occurred on December 23rd, 2015. Industroyer is the first ever known malware specifically designed to attack electrical grids.
TRITON: a malware designed to manipulate industrial Triconex Safety Instrumented System (SIS) controllers. Triconex systems provide emergency shutdown capability for industrial processes. TRITON was developed to prevent safety mechanisms from executing their intended function, resulting in a physical consequence. (Analysing the TRITON industrial malware)
U.S. Escalates Online Attacks on Russia’s Power Grid (Jun 2019): The United States is stepping up digital incursions into Russia’s electric power grid in a warning to President Vladimir V. Putin, current and former government officials said. In interviews over the past three months, the officials described the previously unreported deployment of American computer code inside Russia’s grid.
Introduction
ICS/SCADA are fragile and sensitive systems and any outages may disrupt normal functioning of a city or an entire country. For no reason, ICS should be connected to the Internet, but to save money, a lot of companies allows remote access to these systems.
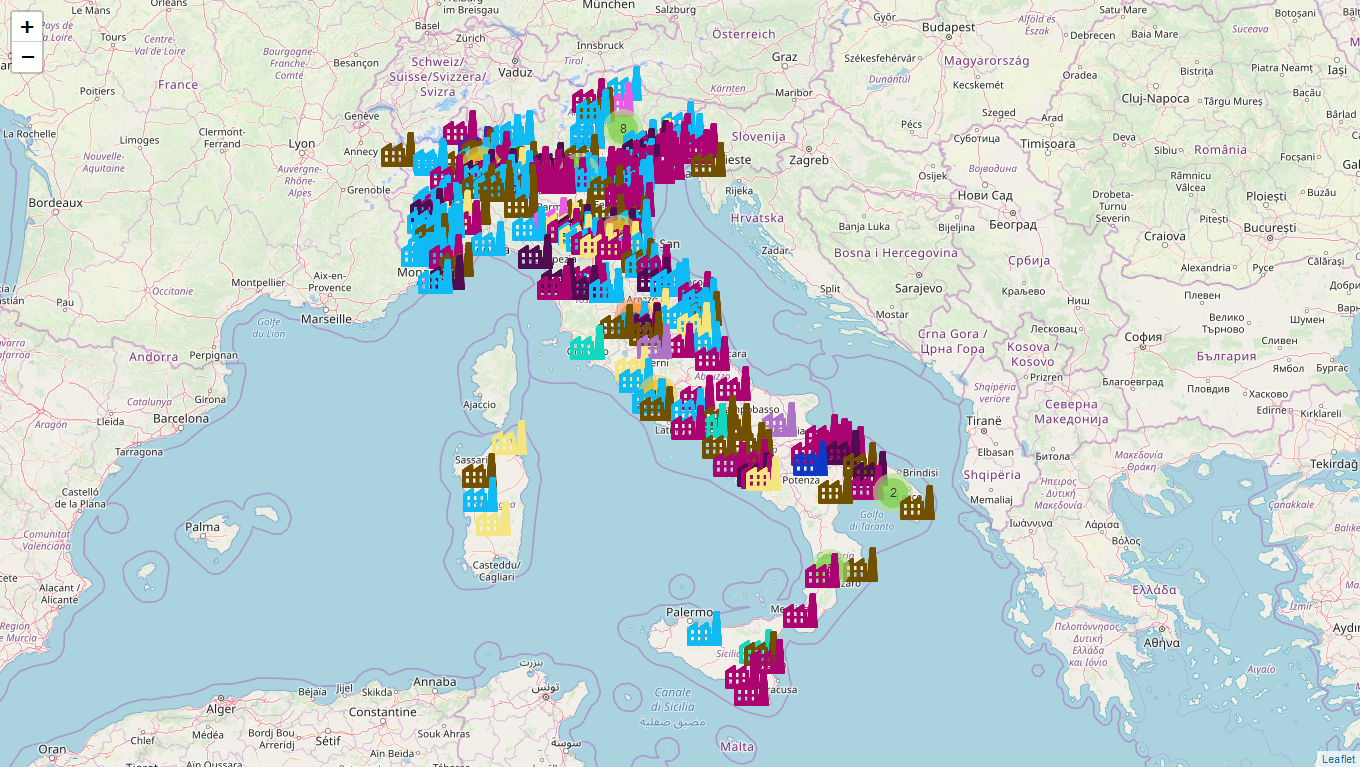
In order to better understand Italy ICS exposure, I’ve decided to perform a “mega-survey” of all the internet facing hosts exposing ICS/SCADA protocols in my country.

Data and Map Generation
I’ve mainly used Shodan, searching for the following devices and protocols. The following protocols are some of the languages that the industrial control systems use to communicate. Many of them were developed before Internet became widely used, which is why Internet-accessible ICS devices don’t always require authentication.
- BACnet (port 47808): is a communications protocol for building automation and control networks. It was designed to allow communication of building automation and control systems for applications such as heating, air-conditioning, lighting, and fire detection systems.
- Codesys: over 250 device manufacturers from different industrial sectors offer automation devices with a CODESYS programming interface. Consequently, thousands of users such as machine or plant builders around the world employ CODESYS for automation tasks.
- DNP3 (port 20000): Distributed Network Protocol is a set of communications protocols used between components in process automation systems. Its main use is in utilities such as electric and water companies.
- EtherNet/IP (port 44818): was introduced in 2001 and is an industrial Ethernet network solution available for manufacturing automation.
- General Electric (product:”general electric”)
- GE Industrial Solution: Service Request Transport Protocol (GE-SRTP) protocol is developed by GE Intelligent Platforms (earlier GE Fanuc) for transfer of data from PLCs.
- HART IP: The HART Communications Protocol (Highway Addressable Remote Transducer Protocol) is an early implementation of Fieldbus, a digital industrial automation protocol. Its most notable advantage is that it can communicate over legacy wiring.
- IEC 60870–5–104
- IEC-104 (port 2404):is one of the IEC 60870 set of standards which define systems used for SCADA in electrical engineering and power system automation applications.
- Mitsubishi Electric (product:“Mitsubishi”): MELSEC-Q Series use a proprietary network protocol for communication. The devices are used by equipment and manufacturing facilities to provide high-speed, large volume data processing and machine control.
- Modbus (port 502): a popular protocol for industrial control systems (ICS). It provides easy, raw access to the control system without requiring any authentication.
- Omron: Factory Interface Network Service (FINS), is a network protocol used by Omron PLCs, over different physical networks like Ethernet, Controller Link, DeviceNet and RS-232C.
- PCWorx: is a protocol and program by Phoenix Contact used by a wide range of industries.
- port:20547,1962 PLC
- port:2455 operating system
- port:9600 response code
- ProConOS:a high-performance PLC run time engine designed for both embedded and PC based control applications.
- Red Lion (port 789 product:”Red Lion Controls”): Crimson v3.0 desktop software’s protocol used when communicating with the Red Lion Controls G306a human machine interface (HMI).
- Siemens S7 (port 102): S7 Communication, a proprietary protocol that runs between programmable logic controllers (PLCs) of the Siemens S7 family.
- Tridium Niagara Fox (ports 1911 and 4911): the Fox protocol, developed as part of the Niagara framework from Tridium, is most commonly seen in building automation systems (offices, libraries, Universities, etc.).
Research
Based on previously filters I was able to enumerate 3630 machines (3568 unique IPs) running different Industrial Control Systems. I also gathered a small sample of geolocation data and plotted them on a map with Kamerka (I love this tool).

The results are an outstanding number of 3630 machines internet facing ICS machines (3568 unique IPs), spanning over 116 unique ISP and 264 cities.



While diving in the dataset I was able to recover some of the products used:
- EY-AS525F001
- EY-RC500F001
- BMX P34 2020
- PCO1000WB0
- INSIGHT
- SAS TSXETY4103
- NiagaraAX Station
- DDC420
- BACnet Direct
- DSM_RTR
- LGR250
- ControlMaestroBACnetDriver
- Eagle
- MS-NAE4510-2
- MS-NAE5510-1
- SAS TSXETY5103
- TM258LF42DT
- BMX NOE 0100
- Red Lion Controls
And many weird things were left exposed:
- Museums
- Hotels
- Terme/Swimming pools
- Supermarkets
- Thermal Power Plant
- Microbiology Stuff
- Wine Production Systems
Some of the exposed devices where a bit worrisome, especially for their geo-localization, as the following one:

There were also numerous “devices” geo-localized in the middle of an Italian lake…
Another aspect that it’s something to do not underestimate while speaking of ICS security is the security of all the other services exposed on the same IPs. A lot of machines have additional open ports, mostly HTTP/s with login pages, FTP, SSH, VNC, RDP, Telnet, SNMP which reveals manufacturer and version of the software, further amplifying the attack surface.
Conclusion
It’s time to rise the security bar for the ICS/SCADA field, not only for manufactures but also for companies empowering them. Functioning of entire countries depends of these devices and lives may be in danger in case of outage or intentional cyber-attacks.
I’ve said the exact same thing more than two year ago speaking at one conference: “Italy will hardly compete with other countries, within the cyber security field, only if we’ll start training people regarding cyber security risks, create appropriate training paths and careers, and level salaries for this field. This last step is essential, without it everything will be useless, we will spend a lot of energy (money and time) developing highly trained personal that will leave the country for a better job salary around the world”.
Common Terms
- ICS: Industrial Control System
ICS environment are often a hybrid of DCS and SCADA wherein attributes from both systems are incorporated.
- SCADA: Supervisory Control and Data Acquisition
SCADA systems are composed of devices (generally Programmable Logic Controllers (PLC) or other commercial hardware modules) that are distributed in various locations. SCADA systems can acquire and transmit data and are integrated with a Human Machine Interface (HMI) that provides centralized monitoring and control for numerous process inputs and outputs.
The primary purpose of using SCADA is for long distance monitoring and control of field sites through a centralized control system. In lieu of workers having to travel long distances to perform tasks or gather data, a SCADA system can automate this task. Field devices control local operations such as opening or closing of valves and breakers, collecting data from the sensor systems, and monitoring the local environment for alarm conditions.
SCADA systems are commonly used in industries involving pipeline monitoring and control, water treatment centres and distribution, and electrical power transmission and distribution.
- PLC: Programmable Logic Controller
This is a type of hardware that is used in both DCS and SCADA systems as a control component of an overall system. It also provides local management of processes being run through feedback control devices such as sensors and actuators.
In SCADA, a PLC provides the same functionality as Remote Terminal Units (RTU). In DCS, PLCs are used as local controllers within a supervisory control scheme. PLCs are also implemented as primary components in smaller control system configurations.
- DCS: Distributed Control System
Systems that are used to control production systems that are found in one location. In a DCS, a setpoint is sent to the controller that is capable of instructing valves, or even an actuator, to operate in such a way that the desired setpoint is maintained. Data from the field can either be stored for future reference, used for simple process control, or even used for advanced control strategies with data from another part of the plant.
Each DCS uses a centralized supervisory control loop to manage multiple local controllers or devices that are part of the overall production process. This gives industries the ability to quickly access production and operation data. And by using multiple devices within the production process, a DCS can reduce the impact of a single fault on the overall system.
A DCS is also commonly used in industries such as manufacturing, electric power generation, chemical manufacturing, oil refineries, and water and wastewater treatment.
- RTU: Remote Terminal Unit
An RTU is a microprocessor-controlled field device that receives commands and sends information back to the MTU.
- HMI: Human Machine Interface
A graphical user interface (GUI) application that allows interaction between the human operator and the controller hardware. It can also display status information and historical data gathered by the devices in the ICS environment. It is also used to monitor and configure setpoints, control algorithms, and adjust and establish parameters in the controllers.