1Dec-22
21Jul-22
Browser Exploitation: Firefox Integer Overflow – CVE-2011-2371
In case you're wondering why I'm not posting as regularly as before, with the new year, I've finally transitioned into a fully offensive vulnerability research and exploit development role at Exodus Intelligence that fulfilled my career dream (BTW, we're currently hiring). In the last couple of months, I've worked on some exciting and challenging bugs. Hopefully, these bugs will be featured on my blog post as soon as I am allowed to share them and after the vendors issue a...
17Mar-21
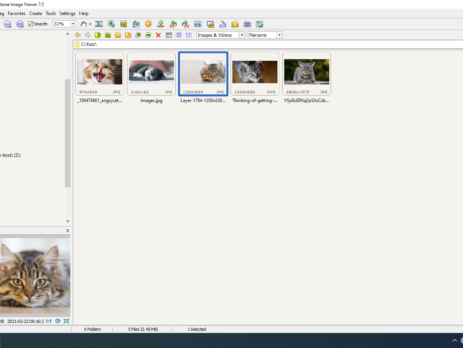
Fuzzing: FastStone Image Viewer & CVE-2021-26236
This blog post is a re-post of the original article “Fuzzing: FastStone Image Viewer & CVE-2021-26236” that I have written for Yarix on YLabs. Introduction In my precedent blog post I’ve introduced “fuzzing” from a theoretical point of view. As I’ve previously anticipated, today I’m going to disclose the fuzzing methodology, process and samples that led me to discover five different vulnerabilities in FastStone Image Viewer v.<=7.5. I’ll also go over the root cause analysis of CVE-2021-26236 and how to achieve Arbitrary...
18Nov-20
Tivoli Madness
TL; DR: this blog post serves as an advisory for both: CVE-2020-28054: An Authorization Bypass vulnerability affecting JamoDat – TSMManager Collector v. <= 6.5.0.21 A Stack Based Buffer Overflow affecting IBM Tivoli Storage Manager - ITSM Administrator Client Command Line Administrative Interface (dsmadmc.exe) Version 5, Release 2, Level 0.1. Unfortunately, after I had one of the rudest encounters with an Hackerone’s triager, these are the takeaways: IBM Tivoli Storage Manager has reached its end of life support and will not be...
13May-20
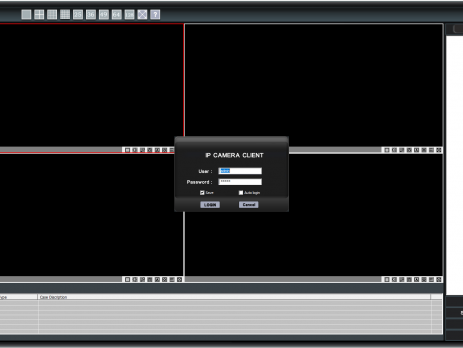
A tale of a kiosk escape: ‘Sricam CMS’ Stack Buffer Overflow
TL;DR: Shenzhen Sricctv Technology Sricam CMS (SricamPC.exe) <= v.1.0.0.53(4) and DeviceViewer (DeviceViewer.exe) <= v.3.10.12.0 (CVE-2019-11563) are affected by a local Stack Buffer Overflow. By creating a specially crafted "Username" and copying its value in the "User/mail" login field, an attacker will be able to gain arbitrary code execution in the context of the currently logged-in user. Please Note: by default, Sricam CMS requires elevation and runs in High Integrity mode; exploitation of the above software will result in a compromise of...
19May-16