5May-21
17Mar-21
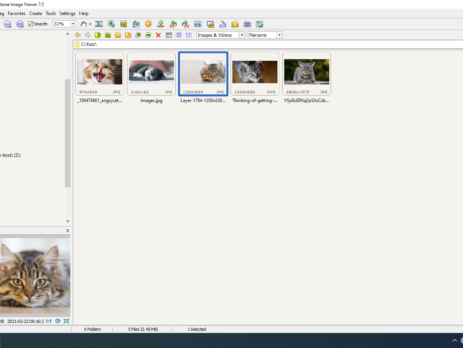
Fuzzing: FastStone Image Viewer & CVE-2021-26236
This blog post is a re-post of the original article “Fuzzing: FastStone Image Viewer & CVE-2021-26236” that I have written for Yarix on YLabs. Introduction In my precedent blog post I’ve introduced “fuzzing” from a theoretical point of view. As I’ve previously anticipated, today I’m going to disclose the fuzzing methodology, process and samples that led me to discover five different vulnerabilities in FastStone Image Viewer v.<=7.5. I’ll also go over the root cause analysis of CVE-2021-26236 and how to achieve Arbitrary...
24Feb-21
Software Testing Methodologies & Approaches to Fuzzing
This blog post is part of a series and a re-posting of the original article “Fuzzing 101” that I have written for Yarix on YLabs. Introduction In this article, I would like to introduce fuzz testing as part of a vast overview of software testing approaches used to discover bugs and vulnerabilities within applications, protocols, file formats and more. Application Security With an ever-increasing number of vulnerabilities discovered during the years, many organizations still spend little budget and effort to produce and ensure code...
18Nov-20
Tivoli Madness
TL; DR: this blog post serves as an advisory for both: CVE-2020-28054: An Authorization Bypass vulnerability affecting JamoDat – TSMManager Collector v. <= 6.5.0.21 A Stack Based Buffer Overflow affecting IBM Tivoli Storage Manager - ITSM Administrator Client Command Line Administrative Interface (dsmadmc.exe) Version 5, Release 2, Level 0.1. Unfortunately, after I had one of the rudest encounters with an Hackerone’s triager, these are the takeaways: IBM Tivoli Storage Manager has reached its end of life support and will not be...
7Oct-20
.NET Grey Box Approach: Source Code Review & Dynamic Analysis
Following a recent engagement, I had the opportunity to check and verify some possible vulnerabilities on an ASP .NET application. Despite not being the deepest technical nor innovative blog post you could find on the net, I have decided to post it anyway in order to explain the methodology I adopt to verify possible vulnerabilities. If you are into grey-box approach (Source Code Review and Dynamic Analysis, SAST/DAST), new to ASP .NET applications or you are planning to take AWAE, you...
13May-20
A tale of a kiosk escape: ‘Sricam CMS’ Stack Buffer Overflow
TL;DR: Shenzhen Sricctv Technology Sricam CMS (SricamPC.exe) <= v.1.0.0.53(4) and DeviceViewer (DeviceViewer.exe) <= v.3.10.12.0 (CVE-2019-11563) are affected by a local Stack Buffer Overflow. By creating a specially crafted "Username" and copying its value in the "User/mail" login field, an attacker will be able to gain arbitrary code execution in the context of the currently logged-in user. Please Note: by default, Sricam CMS requires elevation and runs in High Integrity mode; exploitation of the above software will result in a compromise of...
8Apr-20
Tabletopia: from XSS to RCE
During this period of social isolation, a friend of mine proposed to play some online "board games". He proposed “Tabletopia”: a cool sandbox virtual table with more than 800 board games. Tabletopia is both accessible from its own website and from the Steam’s platform. While my friends decided to play from their browser, I’ve opted for the Steam version. We joined a room and started a game; at one point we were messing around with some in-game cards when , for no...
24Apr-19
Rubyzip insecure ZIP handling & Metasploit RCE (CVE-2019-5624)
This is a re-posting of the original article "On insecure zip handling, Rubyzip and Metasploit RCE (CVE-2019-5624)" that I have wrote on Doyensec During one of our projects we had the opportunity to audit a Ruby-on-Rails (RoR) web application handling zip files using the Rubyzip gem. Zip files have always been an interesting entrypoint to triggering multiple vulnerability types, including path traversals and symlink file overwrite attacks. As the library under testing had symlink processing disabled, we focused on path traversal...
30Aug-18
Telegram Secret Chat Bug
For whom is following me on Twitter this is not a news, yesterday I was complaining about a Telegram “Feature” in the secret chat context, while for whom doesn’t this should serve as a write-up of the bug that I have discovered (The bug is nothing fancy but something I think people should, at least, know). Telegram Secret Chat If you are not practical with the concept of Telegram’s Secret Chat: “Secret chats are meant for people who want more secrecy than the...
20Jul-18