23Dec-19
2Oct-19
SolarPuttyDecrypt
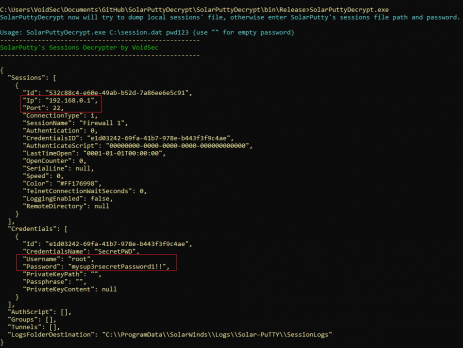
During a recent Red Team engagement, I was able to become domain admin on the client’s network; I decided to investigate further into the “sys admin” workstations and management network in order to recover more information about the network topology and assets, dumping more password and gaining access to firewalls/switches and servers’ VLANs. Enumerating the sysadmin’s workstations, I discovered a windows tool used to connect via SSH. TL;DR SolarPuttyDecrypt is a post-exploitation/forensics tool to decrypt SolarPuTTY's sessions files and retrieve plain-text credentials. It...
19Jun-19
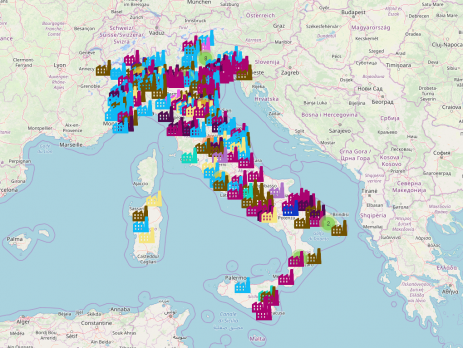
State of Industrial Control Systems (ICS) in Italy
Industrial Control System, what are they? TL;DR: In a nutshell, Industrial control systems (ICS) are “computers” (PLC) that control the world around you. They're responsible for managing the air conditioning in your office, the turbines at a power plant, the lighting at the theatre or the robots at a factory Industrial Control System (ICS) is a general term used to describe several types of control systems and associated instrumentation used for industrial process control. Such systems can range from a few modular panel-mounted...
27Mar-18
VPN Leak
(Edited on 06/04: in order to reflect the actual situation) TL:DR: VPN leaks users’ IPs via WebRTC. I’ve tested hundred VPN and Proxy providers and 19 of them leaks users’ IPs via WebRTC (16%) You can check if your VPN leaks visiting: http://ip.voidsec.com Here you can find the complete list of the VPN providers that I’ve tested: https://docs.google.com/spreadsheets/d/1Nm7mxfFvmdn-3Az-BtE5O0BIdbJiIAWUnkoAF_v_0ug/edit#gid=0 Add a comment or send me a tweet if you have updated results for any of the VPN which I am missing details. (especially...
30May-17
VoidSec CTF: Secure the Flag – Writeup
It has been a while since my last blog post, so I’m (finally) writing the write-up of the: VoidSec CTF Secure the flag. The CTF was made possible thanks to the sponsorship with Bitdefender that put some licenses for its product as a prize for the first three winners. This CTF was web based, no binary exploitation nor reverse engineering and/or crypto was involved. Before I dive into deep, let me explain what was the goal of this CTF and why it is...
3Jul-16
Cybersecurity in Italy
First of all, a small disclaimer: any statement inside this article is based on my own personal point of view. I deliberately generalized and I am aware of the presence of certain exceptions in my country, but this sum up my opinion and there will be people that will be not aligned with those thoughts. After almost 5 years inside the cyber-security field I would like to point out some elements, that according to my point of view, are not working...
1Oct-15
Deep Web & Hacking Communities
Qualche mese fa sono stato intervistato da Pierluigi Paganini per Infosec Institute riguardo l’argomento: Hacking Communities in the Deep Web. Vi propongo quindi la sessione di Q&A tradotta in Italiano, l’articolo originale è ben più vasto di questo piccolo “recap” e ne consiglio la lettura. Si sente spesso parlare di Deep Web, cosa s’intende con questo termine? Il Deep Web è l’insieme di tutti i contenuti internet non indicizzati dai motori di ricerca e pertanto difficilmente raggiungibili dagli utenti standard. Sovente viene utilizzato...
12Apr-15
Android (Un)Security Guidelines
Venerdì 10 Aprile si è concluso a Torino il DroidCon: il congresso Europeo più importante per gli sviluppatori del sistema operativo Android e ritrovo per tutti gli appassionati. Quest’anno l’evento ha raggiunto il traguardo di circa 700 partecipanti e 70 speaker. Noi di VoidSec siamo stati relatori del talk: Android (Un)Security Guidelines Cosa fare, ma soprattutto, cosa non fare durante il ciclo di sviluppo di un'applicazione Android. In questo talk abbiamo mostrato quali sono le possibili problematiche e i vettori di attacco nello scenario Android,...
11Mar-15
Panoramica degli Attacchi 2014
In quest’articolo voglio riassumere brevemente e per settore alcuni degli attacchi informatici che, a mio parere, risultano essere tra i più significativi dell’anno 2014. In particolare, la prossima settimana a Milano, il 17,18 e 19 Marzo si terrà il Security Summit, una manifestazione dedicata alla sicurezza delle informazioni, delle reti e dei sistemi informatici che, da anni, accoglie i partecipanti con contenuti e approfondimenti sull’evoluzione tecnologica del mercato. Durante il Summit verrà presentato il Rapporto Clusit 2015, rapporto che presenta una panoramica...
1Feb-15