16Dec-21
29Sep-21
Crucial’s MOD Utility LPE – CVE-2021-41285
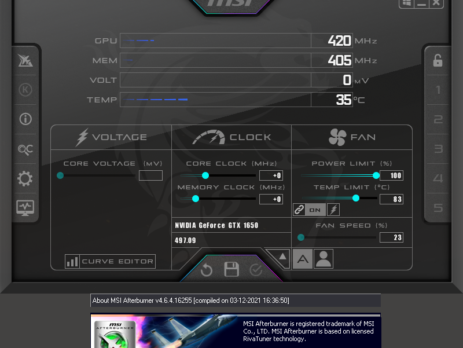
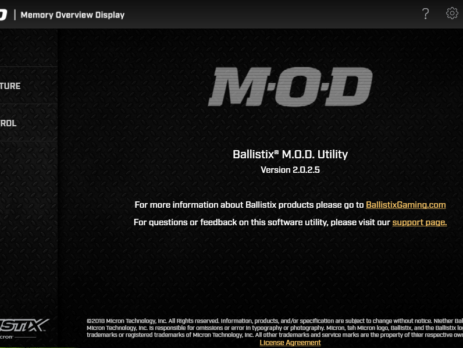
Crucial Ballistix MOD Utility is a software product that can be used to customize and control gaming systems, specifically LED colours and patterns, memory, temperature, and overclock. During my vulnerability research, I’ve discovered that this software utilizes a driver, MODAPI.sys, containing multiple vulnerabilities and allowing an attacker to achieve local privilege escalation from a low privileged user to NT AUTHORITY\SYSTEM. This blog post is a re-post of the original article “Crucial’s MOD Utility LPE” that I have written for Yarix on YLabs. Advisory...
5May-21
CVE‑2021‑1079 – NVIDIA GeForce Experience Command Execution
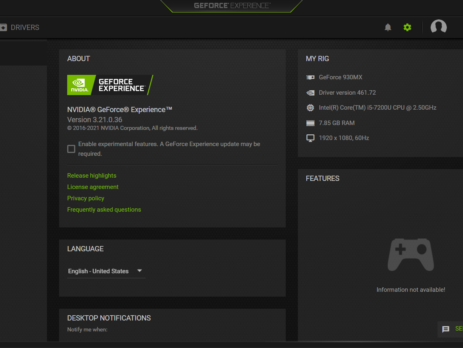
NVIDIA GeForce Experience (GFE) v.<= 3.21 is affected by an Arbitrary File Write vulnerability in the GameStream/ShadowPlay plugins, where log files are created using NT AUTHORITY\SYSTEM level permissions, which lead to Command Execution and Elevation of Privileges (EoP). NVIDIA Security Bulletin – April 2021 NVIDIA Acknowledgements Page This blog post is a re-post of the original article “Chaining Bugs: CVE‑2021‑1079 - NVIDIA GeForce Experience (GFE) Command Execution” that I have written for Yarix on YLabs. Introduction Some time ago I was looking for...
17Mar-21
Fuzzing: FastStone Image Viewer & CVE-2021-26236
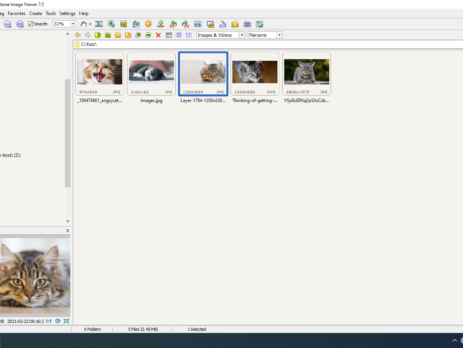
This blog post is a re-post of the original article “Fuzzing: FastStone Image Viewer & CVE-2021-26236” that I have written for Yarix on YLabs. Introduction In my precedent blog post I’ve introduced “fuzzing” from a theoretical point of view. As I’ve previously anticipated, today I’m going to disclose the fuzzing methodology, process and samples that led me to discover five different vulnerabilities in FastStone Image Viewer v.<=7.5. I’ll also go over the root cause analysis of CVE-2021-26236 and how to achieve Arbitrary...
18Nov-20
Tivoli Madness
TL; DR: this blog post serves as an advisory for both: CVE-2020-28054: An Authorization Bypass vulnerability affecting JamoDat – TSMManager Collector v. <= 6.5.0.21 A Stack Based Buffer Overflow affecting IBM Tivoli Storage Manager - ITSM Administrator Client Command Line Administrative Interface (dsmadmc.exe) Version 5, Release 2, Level 0.1. Unfortunately, after I had one of the rudest encounters with an Hackerone’s triager, these are the takeaways: IBM Tivoli Storage Manager has reached its end of life support and will not be...
11Aug-20
CVE-2020-1337 – PrintDemon is dead, long live PrintDemon!
Banner Image by Sergio Kalisiak TL; DR: I will explain, in details, how to trigger PrintDemon exploit and dissect how I’ve discovered a new 0-day; Microsoft Windows EoP CVE-2020-1337, a bypass of PrintDemon’s recent patch via a Junction Directory (TOCTOU). After Yarden Shafir’s & Alex Ionescu’s posts (PrintDemon, FaxHell) and their call to action, I’ve started diving into the PrintDemon exploit. PrintDemon is the catching name for Microsoft CVE-2020-1048: Windows Print Spooler Elevation of Privilege Vulnerability which is affecting (according to Microsoft),...
13May-20
A tale of a kiosk escape: ‘Sricam CMS’ Stack Buffer Overflow
TL;DR: Shenzhen Sricctv Technology Sricam CMS (SricamPC.exe) <= v.1.0.0.53(4) and DeviceViewer (DeviceViewer.exe) <= v.3.10.12.0 (CVE-2019-11563) are affected by a local Stack Buffer Overflow. By creating a specially crafted "Username" and copying its value in the "User/mail" login field, an attacker will be able to gain arbitrary code execution in the context of the currently logged-in user. Please Note: by default, Sricam CMS requires elevation and runs in High Integrity mode; exploitation of the above software will result in a compromise of...
8Apr-20
Tabletopia: from XSS to RCE
During this period of social isolation, a friend of mine proposed to play some online "board games". He proposed “Tabletopia”: a cool sandbox virtual table with more than 800 board games. Tabletopia is both accessible from its own website and from the Steam’s platform. While my friends decided to play from their browser, I’ve opted for the Steam version. We joined a room and started a game; at one point we were messing around with some in-game cards when , for no...
19Jun-19
State of Industrial Control Systems (ICS) in Italy
Industrial Control System, what are they? TL;DR: In a nutshell, Industrial control systems (ICS) are “computers” (PLC) that control the world around you. They're responsible for managing the air conditioning in your office, the turbines at a power plant, the lighting at the theatre or the robots at a factory Industrial Control System (ICS) is a general term used to describe several types of control systems and associated instrumentation used for industrial process control. Such systems can range from a few modular panel-mounted...
24Apr-19