18Jan-24
15Jun-23
Reverse Engineering Terminator aka Zemana AntiMalware/AntiLogger Driver
Recently, a threat actor (TA) known as SpyBot posted a tool, on a Russian hacking forum, that can terminate any antivirus/Endpoint Detection & Response (EDR/XDR) software. IMHO, all the hype behind this announcement was utterly unjustified as it is just another instance of the well-known Bring Your Own Vulnerable Driver (BYOVD) attack technique: where a legitimate signed driver is dropped on victims’ machine and later used to disable security solutions and/or deliver additional payloads. This technique requires administrative...
18Jan-23
SANS SEC760: Advanced Exploit Development for Penetration Testers – Review
In July 2022, I took the SANS SEC 760 class in Berlin. I always promised myself and some close friends to write a review, but I didn't have the time until the Christmas break. This blog post aims to be a day-by-day review of the SANS SEC760 course content and its CTF, NetWars tournament and on-demand package.SANS SEC760
Looking at SANS's website, SEC 760 should teach skills required to reverse-engineer applications in order to find vulnerabilities, perform fuzzing and...
22Dec-22
Naughty List Challenge Write-Up – X-MAS CTF
As the last post of the year, I decided to do something chill and a bit “off-topic” from my usual content. As the festivities are approaching, I have a bit more free time to dedicate to different stuff, like helping some friends with CTFs and such. I’ve decided to post about this specific challenge because since it wasn’t the most complex nor the one with the most shenanigans to flex about, it likely wouldn’t get any write-ups. But it’s a perfect...
1Dec-22
Windows Exploitation Challenge – Blue Frost Security 2022 (Ekoparty)
Last month, during Ekoparty, Blue Frost Security published a Windows challenge. Since having a Windows exploitation challenge, is one of a kind in CTFs, and since I've found the challenge interesting and very clever, I've decided to post about my reverse engineering and exploitation methodology.Challenge Requests
Only Python solutions without external libraries will be accepted The goal is to execute the Windows Calculator (calc.exe) The solution should work on Windows 10 or Windows 11 Process continuation is...
21Jul-22
Browser Exploitation: Firefox Integer Overflow – CVE-2011-2371
In case you're wondering why I'm not posting as regularly as before, with the new year, I've finally transitioned into a fully offensive vulnerability research and exploit development role at Exodus Intelligence that fulfilled my career dream (BTW, we're currently hiring). In the last couple of months, I've worked on some exciting and challenging bugs. Hopefully, these bugs will be featured on my blog post as soon as I am allowed to share them and after the...
20Jan-22
Windows Drivers Reverse Engineering Methodology
With this blog post I’d like to sum up my year-long Windows Drivers research; share and detail my own methodology for reverse engineering (WDM) Windows drivers, finding some possible vulnerable code paths as well as understanding their exploitability. I've tried to make it as "noob-friendly" as possible, documenting all the steps I usually perform during my research and including a bonus exercise for the readers.Setting up the lab
While in the past, setting up a lab for kernel...
16Dec-21
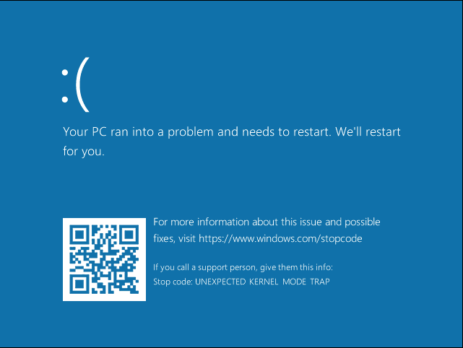
Merry Hackmas: multiple vulnerabilities in MSI’s products
This blog post serves as an advisory for a couple of MSI’s products that are affected by multiple high-severity vulnerabilities in the driver components they are shipped with. All the vulnerabilities are triggered by sending specific IOCTL requests and will allow to: Directly interact with physical memory via the MmMapIoSpace function call, mapping physical memory into a virtual address user-space. Read/write Model-Specific Registers (MSRs) via the __readmsr/__writemsr functions calls. Read/write 1/2/4 bytes to or from an IO port. An attacker could exploit...
27Oct-21
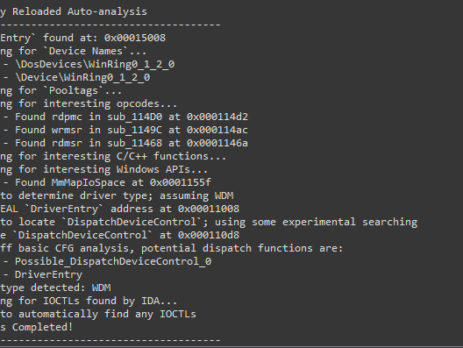
Driver Buddy Reloaded
As part of my continuous security research journey, during this year I’ve spent a good amount of time reverse-engineering Windows drivers and exploiting kernel-mode related vulnerabilities. While in the past there were (as far as I know), at least two good IDA plugins aiding in the reverse engineering process: DriverBuddy of NCC Group. win_driver_plugin of F-Secure. unfortunately, nowadays, they are both rusty, out of date and broken on the latest version of IDA. They relied on...
29Sep-21