18Jan-24
20Jan-22
Windows Drivers Reverse Engineering Methodology
With this blog post I’d like to sum up my year-long Windows Drivers research; share and detail my own methodology for reverse engineering (WDM) Windows drivers, finding some possible vulnerable code paths as well as understanding their exploitability. I've tried to make it as "noob-friendly" as possible, documenting all the steps I usually perform during my research and including a bonus exercise for the readers. Setting up the lab While in the past, setting up a lab for kernel debugging was a...
27Oct-21
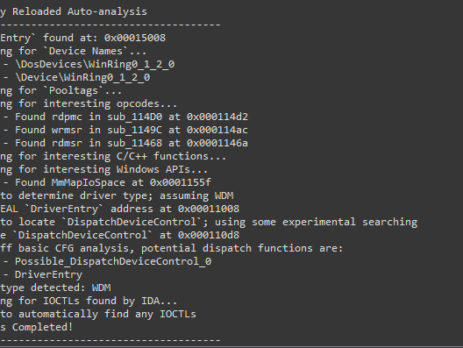
Driver Buddy Reloaded
As part of my continuous security research journey, during this year I’ve spent a good amount of time reverse-engineering Windows drivers and exploiting kernel-mode related vulnerabilities. While in the past there were (as far as I know), at least two good IDA plugins aiding in the reverse engineering process: DriverBuddy of NCC Group. win_driver_plugin of F-Secure. unfortunately, nowadays, they are both rusty, out of date and broken on the latest version of IDA. They relied on external dependencies, were lacking documentation and...
29Sep-21
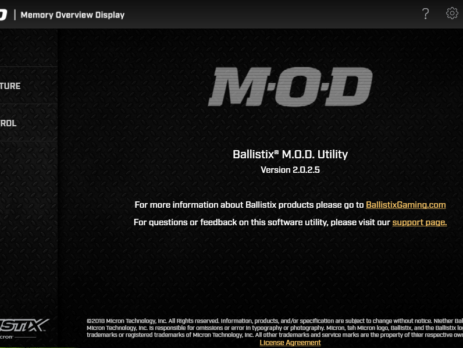
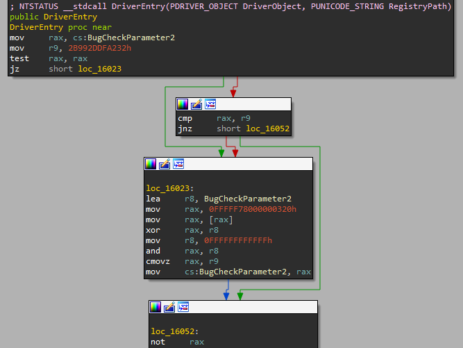
Crucial’s MOD Utility LPE – CVE-2021-41285
Crucial Ballistix MOD Utility is a software product that can be used to customize and control gaming systems, specifically LED colours and patterns, memory, temperature, and overclock. During my vulnerability research, I’ve discovered that this software utilizes a driver, MODAPI.sys, containing multiple vulnerabilities and allowing an attacker to achieve local privilege escalation from a low privileged user to NT AUTHORITY\SYSTEM. This blog post is a re-post of the original article “Crucial’s MOD Utility LPE” that I have written for Yarix on YLabs. Advisory...
19May-21
Reverse Engineering & Exploiting Dell CVE-2021-21551
At the beginning of the month, Sentinel One disclosed five high severity vulnerabilities in Dell’s firmware update driver. As the described vulnerability appeared not too complicated to exploit, a lot of fellow security researchers started weaponizing it. I was one of, if not the first tweeting about weaponizing it into a _SEP_TOKEN_PRIVILEGES overwrite exploit, and with this blog post I would like to write down my thoughts process when dealing with n-day exploit writing. It’s a didactic blog post but keep...
14Apr-21
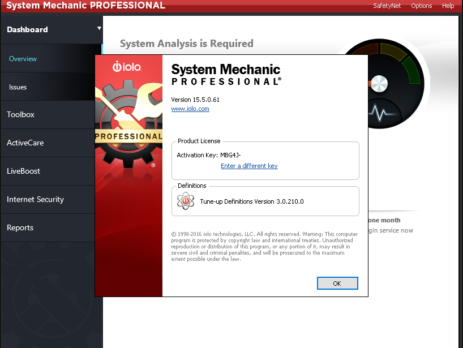
Exploiting System Mechanic Driver
Last month we (last & VoidSec) took the amazing Windows Kernel Exploitation Advanced course from Ashfaq Ansari (@HackSysTeam) at NULLCON. The course was very interesting and covered core kernel space concepts as well as advanced mitigation bypasses and exploitation. There was also a nice CTF and its last exercise was: “Write an exploit for System Mechanics”; no further hints were given. We took the challenge as that was a good time to test our newly acquired knowledge and understanding of the...
17Jul-19