18May-18
18Sep-17
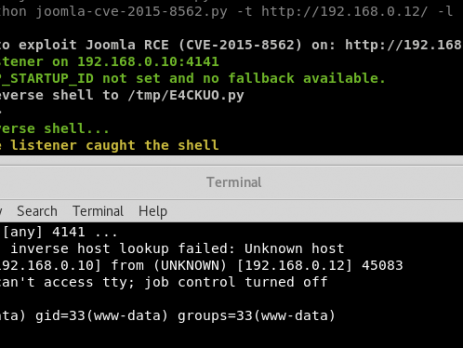
Analysis of the Joomla RCE (CVE-2015-8562)
Recently, during a penetration test I have found a vulnerable installation of the Joomla CMS. Yes, I already know that this vulnerability is quite old and that there is a ready to use Metasploit module but here is the catch: the module and other scripts available on internet weren’t working against my environment, furthermore, during the last year a lot of new vulnerabilities rely on the PHP Object Injection and Serialize/Unserialize. That's the reason why I thought it was a good...
30May-17
VoidSec CTF: Secure the Flag – Writeup
It has been a while since my last blog post, so I’m (finally) writing the write-up of the: VoidSec CTF Secure the flag. The CTF was made possible thanks to the sponsorship with Bitdefender that put some licenses for its product as a prize for the first three winners. This CTF was web based, no binary exploitation nor reverse engineering and/or crypto was involved. Before I dive into deep, let me explain what was the goal of this CTF and why it is...
4May-16
ImageTragick PoC
ImageMagick Is On Fire — CVE-2016–3714 There are multiple vulnerabilities in ImageMagick, a package commonly used by web services to process images. One of the vulnerabilities can lead to remote code execution (RCE) if you process user submitted images. The exploit for this vulnerability is being used in the wild. A number of image processing plugins depend on the ImageMagick library, including, but not limited to, PHP’s imagick, Ruby’s rmagick and paperclip, and nodejs’s imagemagick. For more information about this vulnerability visit: https://imagetragick.com/ or this...
21Apr-16
Phorum – Full Disclosure
Reporter VoidSec Security Team Advisory VoidSec-16-002 Date of contact 03-03-16 2nd date of contact 16-03-16 3rd date of contact 04-04-16 Vendor last reply 03-03-16 Date of public disclosure 21-04-16 Product Phorum Open Source PHP Forum Software Version 5.2.20 Download the Report [EN] Introduction The purpose of the present project is to assess the security posture of some important aspects of Phorum Forum Software. Phorum is open source forum software with a penchant for speed. Phorum's very flexible hook and module system can satisfy every web master's needs. During the web application security assessment for Phorum, VoidSec assessed the following systems using...
19Apr-16
LinkedIn – CSV Excel formula injection
We are proud to publish an undisclosed vulnerability affecting LinkedIn and in particular its "CSV Export" function. Following our Vulnerability Disclosure Policy Agreement, LinkedIn Security Team has been informed about this specific issue and this vulnerability will be published without a working PoC. LinkedIn's users can exports all their connections into a CSV file, that due to some missing filters (escaping output), could allows an attacker to execute a command on the user machine. An attacker can create a LinkedIn profile embedding a...
13Apr-16
Avactis – Full Disclosure
Advisory: VoidSec-16-001 Date of contact: 19-01-16 2nd date of contact: 23-01-16 Vendor reply: N/A Date of public disclosure: 12-04-16 Product: Avactis PHP Shopping Cart Version: 4.7.9.Next.47900 Vendor: Avactis Download the Report [EN] Introduction Avactis is an open source ecommerce Shopping Cart software. The purpose of the present project is to assess the security posture of some important aspects of Avactis PHP Shopping Cart. The activity is performed through Web Application Penetration Test using Grey Box approach. Vulnerabilities: Spreading of Files with Malicious Extensions on Upload New Design and Execution in some circumstances Non-Admin PHP Shell...
18Jun-15
Minds.com – Full Disclosure
Advisory: VoidSec-15-002 Disclosure date: June18, 2015 Vendor: Minds.com Advisory sent: June 17, 2015 Paolo Stagno ( aka voidsec – [email protected] ) Luca Poletti ( aka kalup – [email protected] ) Download the Report [EN] Introduction In those last days a new social network called minds is getting attention over the internet, it aims to give transparency and protection to user data. Thanks to those last two points the new site has attracted the support of online activists including the hacking collective Anonymous. We have then decided to give a look to that amazing platform,...
17Jun-15
HTML5 Injection
Mattia Reggiani è un appassionato di Offensive Security, laureato in Sicurezza Informatica presso l'Università degli Studi di Milano e certificato CEH. Interessato in ethical hacking, forensics analysis e web application security, attualmente svolge l'attività di IT Security consultant. L'introduzione e la recente diffusione di HTML5 come nuovo linguaggio per le pagine Web, ha sollevato nuove vulnerabilità a causa d’implementazioni errate di questa tecnologia. Nel presente articolo sarà descritta la vulnerabilità HTML5 Injection e saranno mostrati scenari reali nella quale è possibile sfruttarla...
21Apr-15