25Aug-21
28Jul-21
Root Cause Analysis of a Printer’s Drivers Vulnerability CVE-2021-3438
Last week SentinelOne disclosed a "high severity" flaw in HP, Samsung, and Xerox printer's drivers (CVE-2021-3438); the blog post highlighted a vulnerable strncpy operation with a user-controllable size parameter but it did not explain the reverse engineering nor the exploitation phase of the issue. With this blog post, I would like to analyse the vulnerability and its exploitability. This blog post is a re-post of the original article “Root Cause Analysis of a Printer's Driver Vulnerability” that I have written for...
19May-21
Reverse Engineering & Exploiting Dell CVE-2021-21551
At the beginning of the month, Sentinel One disclosed five high severity vulnerabilities in Dell’s firmware update driver. As the described vulnerability appeared not too complicated to exploit, a lot of fellow security researchers started weaponizing it. I was one of, if not the first tweeting about weaponizing it into a _SEP_TOKEN_PRIVILEGES overwrite exploit, and with this blog post I would like to write down my thoughts process when dealing with n-day exploit writing. It’s a didactic blog post but keep...
5May-21
CVE‑2021‑1079 – NVIDIA GeForce Experience Command Execution
NVIDIA GeForce Experience (GFE) v.<= 3.21 is affected by an Arbitrary File Write vulnerability in the GameStream/ShadowPlay plugins, where log files are created using NT AUTHORITY\SYSTEM level permissions, which lead to Command Execution and Elevation of Privileges (EoP). NVIDIA Security Bulletin – April 2021 NVIDIA Acknowledgements Page This blog post is a re-post of the original article “Chaining Bugs: CVE‑2021‑1079 - NVIDIA GeForce Experience (GFE) Command Execution” that I have written for Yarix on YLabs. Introduction Some time ago I was looking for...
28Apr-21
Malware Analysis: Ragnarok Ransomware
The analysed sample is a malware employed by the Threat Actor known as Ragnarok. The ransomware is responsible for files’ encryption and it is typically executed, by the actors themselves, on the compromised machines. The name of the analysed executable is xs_high.exe, but others have been found used by the same ransomware family (such as xs_normal.exe and xs_remote.exe). The configuration within the malware contains information regarding the encryption activities, from whitelisted countries to the contents of the ransom note. It is...
14Apr-21
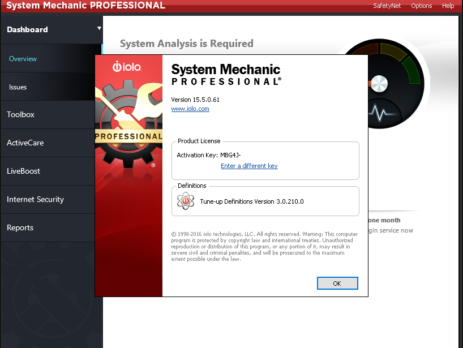
Exploiting System Mechanic Driver
Last month we (last & VoidSec) took the amazing Windows Kernel Exploitation Advanced course from Ashfaq Ansari (@HackSysTeam) at NULLCON. The course was very interesting and covered core kernel space concepts as well as advanced mitigation bypasses and exploitation. There was also a nice CTF and its last exercise was: “Write an exploit for System Mechanics”; no further hints were given. We took the challenge as that was a good time to test our newly acquired knowledge and understanding of the...
17Mar-21
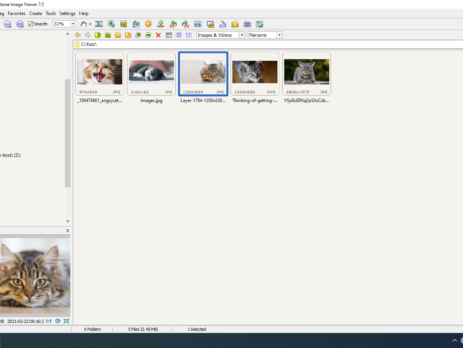
Fuzzing: FastStone Image Viewer & CVE-2021-26236
This blog post is a re-post of the original article “Fuzzing: FastStone Image Viewer & CVE-2021-26236” that I have written for Yarix on YLabs. Introduction In my precedent blog post I’ve introduced “fuzzing” from a theoretical point of view. As I’ve previously anticipated, today I’m going to disclose the fuzzing methodology, process and samples that led me to discover five different vulnerabilities in FastStone Image Viewer v.<=7.5. I’ll also go over the root cause analysis of CVE-2021-26236 and how to achieve Arbitrary...
24Feb-21
Software Testing Methodologies & Approaches to Fuzzing
This blog post is part of a series and a re-posting of the original article “Fuzzing 101” that I have written for Yarix on YLabs. Introduction In this article, I would like to introduce fuzz testing as part of a vast overview of software testing approaches used to discover bugs and vulnerabilities within applications, protocols, file formats and more. Application Security With an ever-increasing number of vulnerabilities discovered during the years, many organizations still spend little budget and effort to produce and ensure code...
11Jan-21
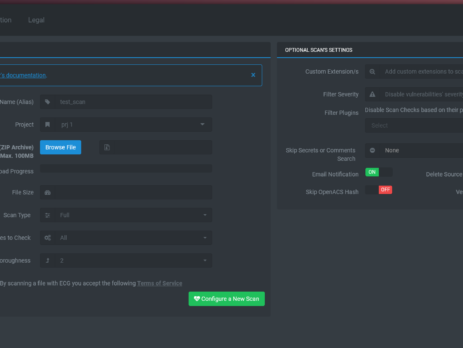
Announcing ECG v2.0
We are proud to announce that ECG got its first major update. ECG: is the first and single commercial solution (Static Source Code Scanner) able to analyze & detect real and complex security vulnerabilities in TCL/ADP source-code. ECG's v2.0 New Features On-Premises Deploy: Scan your code repository on your secure and highly-scalable offline appliance with a local ECG's installation to comply with strict code privacy policies. API Support: Easily integrate ECG's automated security testing into your continuous integration (CI/CD) and delivery tools. Manage your risks...
18Nov-20