20Jul-18
18May-18
GraphQL – Security Overview and Testing Tips
This is a re-posting of the original article "GraphQL - Security Overview and Testing Tips" that I have wrote on Doyensec With the increasing popularity of GraphQL technology we are summarizing some documentation and tips about common security mistakes. What is GraphQL? GraphQL is a data query language developed by Facebook and publicly released in 2015. It is an alternative to REST API. Even if you don’t see any GraphQL out there, it is likely you’re already using it since it’s running on some...
27Mar-18
VPN Leak
(Edited on 06/04: in order to reflect the actual situation) TL:DR: VPN leaks users’ IPs via WebRTC. I’ve tested hundred VPN and Proxy providers and 19 of them leaks users’ IPs via WebRTC (16%) You can check if your VPN leaks visiting: http://ip.voidsec.com Here you can find the complete list of the VPN providers that I’ve tested: https://docs.google.com/spreadsheets/d/1Nm7mxfFvmdn-3Az-BtE5O0BIdbJiIAWUnkoAF_v_0ug/edit#gid=0 Add a comment or send me a tweet if you have updated results for any of the VPN which I am missing details. (especially...
30Dec-17
Uncommon Phishing and Social Engineering Techniques
Sorry if you didn’t hear anything from me for a while but it was a very busy year and the new incoming one will bring a lot of news for me and for the voidsec project, I will speak about it soon in a new blog post. Today I will like to write about some uncommon techniques that I’ve used during social engineering and phishing campaign. Maybe they are not overpowered but they can be pretty useful. Behind the Scene All of these...
18Sep-17
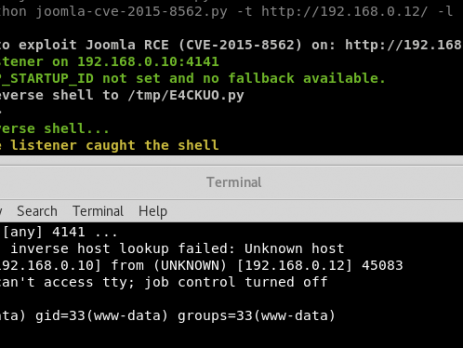
Analysis of the Joomla RCE (CVE-2015-8562)
Recently, during a penetration test I have found a vulnerable installation of the Joomla CMS. Yes, I already know that this vulnerability is quite old and that there is a ready to use Metasploit module but here is the catch: the module and other scripts available on internet weren’t working against my environment, furthermore, during the last year a lot of new vulnerabilities rely on the PHP Object Injection and Serialize/Unserialize. That's the reason why I thought it was a good...
30Jun-17
Descending into Cybercrime
More than an year ago (and before crazy and scary things like WannaCry and Petya happened) I had an idea for a research about the darkest shade of wearing a black hat, by the mean of getting some piece of information and statistics and write an analysis. Not a technical one, but something more like a financial analysis of the cybercrime business model and now I’m going to publish the results (it's even more present now than an year ago...). First...
30May-17
VoidSec CTF: Secure the Flag – Writeup
It has been a while since my last blog post, so I’m (finally) writing the write-up of the: VoidSec CTF Secure the flag. The CTF was made possible thanks to the sponsorship with Bitdefender that put some licenses for its product as a prize for the first three winners. This CTF was web based, no binary exploitation nor reverse engineering and/or crypto was involved. Before I dive into deep, let me explain what was the goal of this CTF and why it is...
27Mar-17
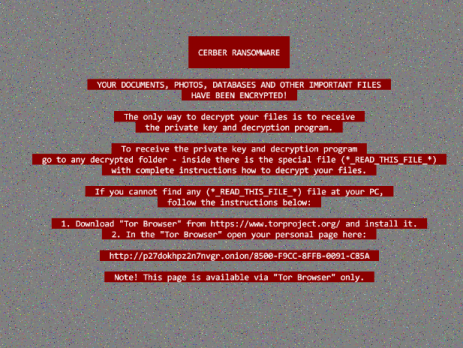
Cerber Dropper Ransomware Analysis
Before the month ends (I’m sorry but my time was really sucked up by planning and developing the HackInBo’s CTF, that I hope you will enjoy) I would like to post this very small and brief analysis of the latest JavaScript dropper used by the Cerber Ransomware in its campaign. I would also like to thank the Hacktive Security’s guys for the following sample: Dropper: MD5 afd5aa687ed3931d39f180f8e15500e1 SHA1 11460389a303e58086a2b7dbdab02437fb001434 SHA256 8b00174be5f9dd6a703bc5327e1be4161cd3922ca9a338889717370b53d4ca71 Cerber Ransomware: MD5 2dd3bd1801989ff6625aa041761cbed3 SHA1 08f28d5a7d32528fdb2b386334669d6b2b4226cb SHA256 a27c202bffde364fc385e41a244649e8e7baaec97c44c45cd02bb59642e1fb0e This time I will not...
13Jan-17
Hacking the DJI Phantom 3
Finally, during Christmas time, I had some spare time to play with my flying beast; I’m speaking about trying to hack my DJI Phantom 3. It was my first time that I operate with drones or similar embedded system and at the beginning I didn’t have any clue about how I could interact with it. The Phantom 3 comes with an aircraft, controller and an Android/iOS app. Let’s start from the beginning: As a first step, I have analysed the protocols, the connection between...
3Nov-16