15Jun-23
20Jan-22
Windows Drivers Reverse Engineering Methodology
With this blog post I’d like to sum up my year-long Windows Drivers research; share and detail my own methodology for reverse engineering (WDM) Windows drivers, finding some possible vulnerable code paths as well as understanding their exploitability. I've tried to make it as "noob-friendly" as possible, documenting all the steps I usually perform during my research and including a bonus exercise for the readers. Setting up the lab While in the past, setting up a lab for kernel debugging was a...
27Oct-21
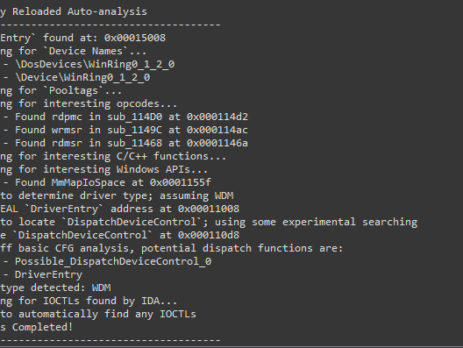
Driver Buddy Reloaded
As part of my continuous security research journey, during this year I’ve spent a good amount of time reverse-engineering Windows drivers and exploiting kernel-mode related vulnerabilities. While in the past there were (as far as I know), at least two good IDA plugins aiding in the reverse engineering process: DriverBuddy of NCC Group. win_driver_plugin of F-Secure. unfortunately, nowadays, they are both rusty, out of date and broken on the latest version of IDA. They relied on external dependencies, were lacking documentation and...
29Sep-21
Crucial’s MOD Utility LPE – CVE-2021-41285
Crucial Ballistix MOD Utility is a software product that can be used to customize and control gaming systems, specifically LED colours and patterns, memory, temperature, and overclock. During my vulnerability research, I’ve discovered that this software utilizes a driver, MODAPI.sys, containing multiple vulnerabilities and allowing an attacker to achieve local privilege escalation from a low privileged user to NT AUTHORITY\SYSTEM. This blog post is a re-post of the original article “Crucial’s MOD Utility LPE” that I have written for Yarix on YLabs. Advisory...
28Jul-21