13May-20
2Apr-20
SLAE – Assignment #7: Custom Shellcode Crypter
Assignment #7: Custom Shellcode Crypter Seventh and last SLAE’s assignment requires to create a custom shellcode crypter. Since I had to implement an entire encryption schema both in python as an helper and in assembly as the main decryption routine, I've opted for something simple. I've chosen the Tiny Encryption Algorithm (TEA) as it does not require large IV or SBOX initialization vectors (adding a huge overhead to my shellcode's decoding routine), because it's tiny and not too complex to re-implement. As always,...
2Apr-20
SLAE – Assignment #6: Polymorphic Shellcode
Assignment #6: Polymorphic Shellcode Sixth SLAE’s assignment requires to create three different (polymorphic) shellcodes version starting from published Shell Storm's examples. I've decided to take this three in exam: http://shell-storm.org/shellcode/files/shellcode-752.php - linux/x86 execve ("/bin/sh") - 21 bytes http://shell-storm.org/shellcode/files/shellcode-624.php - linux/x86 setuid(0) + chmod("/etc/shadow",0666) - 37 bytes http://shell-storm.org/shellcode/files/shellcode-231.php - linux/x86 open cd-rom loop (follows "/dev/cdrom" symlink) - 39 bytes As always, all the code is also available on GitHub. Stay updated, join VoidSec's Telegram Channel: https://t.me/voidsec_updates execve ("/bin/sh") Original: ; http://shell-storm.org/shellcode/files/shellcode-752.php xor ecx, ecx mul ecx push ecx push 0x68732f2f ...
26Mar-20
SLAE – Assignment #5: Metasploit Shellcode Analysis
Assignment #5: Metasploit Shellcode Analysis Fifth SLAE’s assignment requires to dissect and analyse three different Linux x86 Metasploit Payload. Metasploit currently has 35 different payloads but almost half of it are Meterpreter version, thus meaning staged payloads. I’ve then decided to skip meterpreter payloads as they involve multiple stages and higher complexity that will break libemu graph generation (which I find very useful to better explain shellcode’s operations). In this blog we are going to analyse the following shellcodes: linux/x86/shell_find_tag linux/x86/shell_find_port linux/x86/shell/bind_nonx_tcp As always,...
22Jan-20
SLAE – Assignment #2: Reverse TCP Shell
Assignment #2: Reverse TCP Shell Create a shell_reverse_tcp shellcode that connects back to an IP address, on a specific a port and execute a shell. The IP address and port number should be easy configurable. Again, instead of going for the path of writing a C TCP reverse shell from scratch, I decided to generate a raw Metasploit payload and analyze it with libemu. Analyzing the Shellcode All the code is also available on GitHub. This time the analysis will be a lot shorter due...
9Jan-20
SLAE – Assignment #1: Bind TCP Shell
Before attending the Corelan training and the OSCE certification, I’ve decided to start the x86 Assembly Language and Shellcoding on Linux Pentester Academy’s course. The next couple blogs (~7) will contains the assignments’ solutions for the SLAE certification exam. Assignment #1: Bind TCP Shell Create a shell_bind_tcp shellcode that binds to a port and execute a shell on an incoming connection, the port number should be easy to configure. Instead of going for the path of writing a C bind TCP shell from scratch,...
2Oct-19
SolarPuttyDecrypt
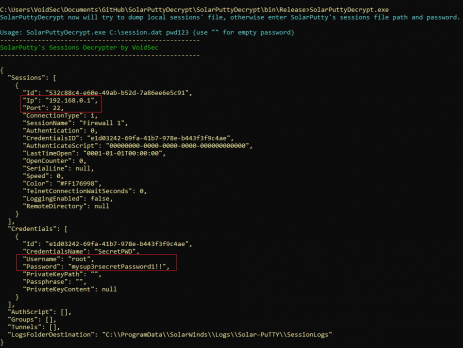
During a recent Red Team engagement, I was able to become domain admin on the client’s network; I decided to investigate further into the “sys admin” workstations and management network in order to recover more information about the network topology and assets, dumping more password and gaining access to firewalls/switches and servers’ VLANs. Enumerating the sysadmin’s workstations, I discovered a windows tool used to connect via SSH. TL;DR SolarPuttyDecrypt is a post-exploitation/forensics tool to decrypt SolarPuTTY's sessions files and retrieve plain-text credentials. It...
24Apr-19
Rubyzip insecure ZIP handling & Metasploit RCE (CVE-2019-5624)
This is a re-posting of the original article "On insecure zip handling, Rubyzip and Metasploit RCE (CVE-2019-5624)" that I have wrote on Doyensec During one of our projects we had the opportunity to audit a Ruby-on-Rails (RoR) web application handling zip files using the Rubyzip gem. Zip files have always been an interesting entrypoint to triggering multiple vulnerability types, including path traversals and symlink file overwrite attacks. As the library under testing had symlink processing disabled, we focused on path traversal...
18Sep-17
Analysis of the Joomla RCE (CVE-2015-8562)
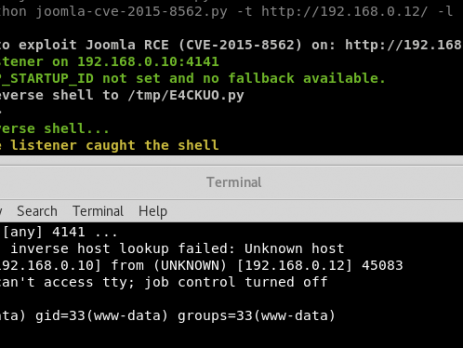
Recently, during a penetration test I have found a vulnerable installation of the Joomla CMS. Yes, I already know that this vulnerability is quite old and that there is a ready to use Metasploit module but here is the catch: the module and other scripts available on internet weren’t working against my environment, furthermore, during the last year a lot of new vulnerabilities rely on the PHP Object Injection and Serialize/Unserialize. That's the reason why I thought it was a good...
19May-16