18Jan-24
1Dec-22
Windows Exploitation Challenge – Blue Frost Security 2022 (Ekoparty)
Last month, during Ekoparty, Blue Frost Security published a Windows challenge. Since having a Windows exploitation challenge, is one of a kind in CTFs, and since I've found the challenge interesting and very clever, I've decided to post about my reverse engineering and exploitation methodology. Challenge Requests Only Python solutions without external libraries will be accepted The goal is to execute the Windows Calculator (calc.exe) The solution should work on Windows 10 or Windows 11 Process continuation is desirable (not mandatory) You...
20Jan-22
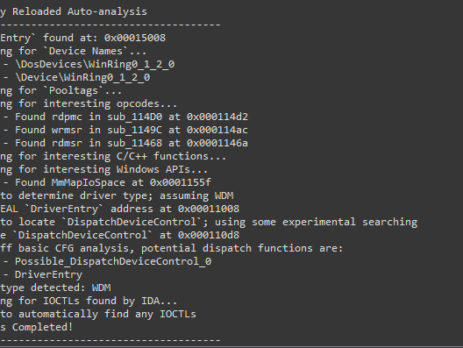
Windows Drivers Reverse Engineering Methodology
With this blog post I’d like to sum up my year-long Windows Drivers research; share and detail my own methodology for reverse engineering (WDM) Windows drivers, finding some possible vulnerable code paths as well as understanding their exploitability. I've tried to make it as "noob-friendly" as possible, documenting all the steps I usually perform during my research and including a bonus exercise for the readers. Setting up the lab While in the past, setting up a lab for kernel debugging was a...
27Oct-21
Driver Buddy Reloaded
As part of my continuous security research journey, during this year I’ve spent a good amount of time reverse-engineering Windows drivers and exploiting kernel-mode related vulnerabilities. While in the past there were (as far as I know), at least two good IDA plugins aiding in the reverse engineering process: DriverBuddy of NCC Group. win_driver_plugin of F-Secure. unfortunately, nowadays, they are both rusty, out of date and broken on the latest version of IDA. They relied on external dependencies, were lacking documentation and...
14Apr-21
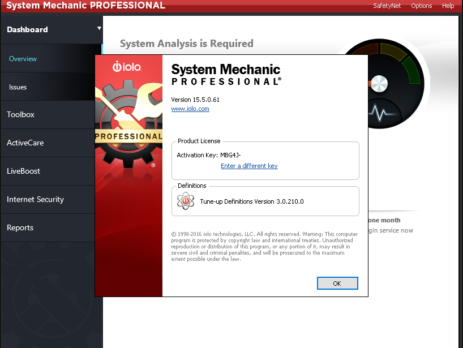
Exploiting System Mechanic Driver
Last month we (last & VoidSec) took the amazing Windows Kernel Exploitation Advanced course from Ashfaq Ansari (@HackSysTeam) at NULLCON. The course was very interesting and covered core kernel space concepts as well as advanced mitigation bypasses and exploitation. There was also a nice CTF and its last exercise was: “Write an exploit for System Mechanics”; no further hints were given. We took the challenge as that was a good time to test our newly acquired knowledge and understanding of the...
2Apr-20
SLAE – Assignment #7: Custom Shellcode Crypter
Assignment #7: Custom Shellcode Crypter Seventh and last SLAE’s assignment requires to create a custom shellcode crypter. Since I had to implement an entire encryption schema both in python as an helper and in assembly as the main decryption routine, I've opted for something simple. I've chosen the Tiny Encryption Algorithm (TEA) as it does not require large IV or SBOX initialization vectors (adding a huge overhead to my shellcode's decoding routine), because it's tiny and not too complex to re-implement. As always,...
2Apr-20
SLAE – Assignment #6: Polymorphic Shellcode
Assignment #6: Polymorphic Shellcode Sixth SLAE’s assignment requires to create three different (polymorphic) shellcodes version starting from published Shell Storm's examples. I've decided to take this three in exam: http://shell-storm.org/shellcode/files/shellcode-752.php - linux/x86 execve ("/bin/sh") - 21 bytes http://shell-storm.org/shellcode/files/shellcode-624.php - linux/x86 setuid(0) + chmod("/etc/shadow",0666) - 37 bytes http://shell-storm.org/shellcode/files/shellcode-231.php - linux/x86 open cd-rom loop (follows "/dev/cdrom" symlink) - 39 bytes As always, all the code is also available on GitHub. Stay updated, join VoidSec's Telegram Channel: https://t.me/voidsec_updates execve ("/bin/sh") Original: ; http://shell-storm.org/shellcode/files/shellcode-752.php xor ecx, ecx mul ecx push ecx push 0x68732f2f ...
26Mar-20
SLAE – Assignment #5: Metasploit Shellcode Analysis
Assignment #5: Metasploit Shellcode Analysis Fifth SLAE’s assignment requires to dissect and analyse three different Linux x86 Metasploit Payload. Metasploit currently has 35 different payloads but almost half of it are Meterpreter version, thus meaning staged payloads. I’ve then decided to skip meterpreter payloads as they involve multiple stages and higher complexity that will break libemu graph generation (which I find very useful to better explain shellcode’s operations). In this blog we are going to analyse the following shellcodes: linux/x86/shell_find_tag linux/x86/shell_find_port linux/x86/shell/bind_nonx_tcp As always,...
17Mar-20
SLAE – Assignment #4: Custom shellcode encoder
Assignment #4: Custom Shellcode Encoder As the 4th SLAE’s assignment I was required to build a custom shellcode encoder for the execve payload, which I did, here how. Stay updated, join VoidSec's Telegram Channel: https://t.me/voidsec_updates Encoder Implementations I’ve decided to not relay on XORing functionalities as most antivirus solutions are now well aware of this encoding schema, the same reason for which I’ve skipped ROT13 and other “rotating” encoding. I thought of using some multiple weird shifting schema but that would have had a...
20Feb-20