Announcing ECG v2.0
Reading Time: 3 minutes
We are proud to announce that ECG got its first major update.
ECG: is the first and single commercial solution (Static Source Code Scanner) able to analyze & detect real and complex security vulnerabilities in TCL/ADP source-code.
ECG’s v2.0 New Features
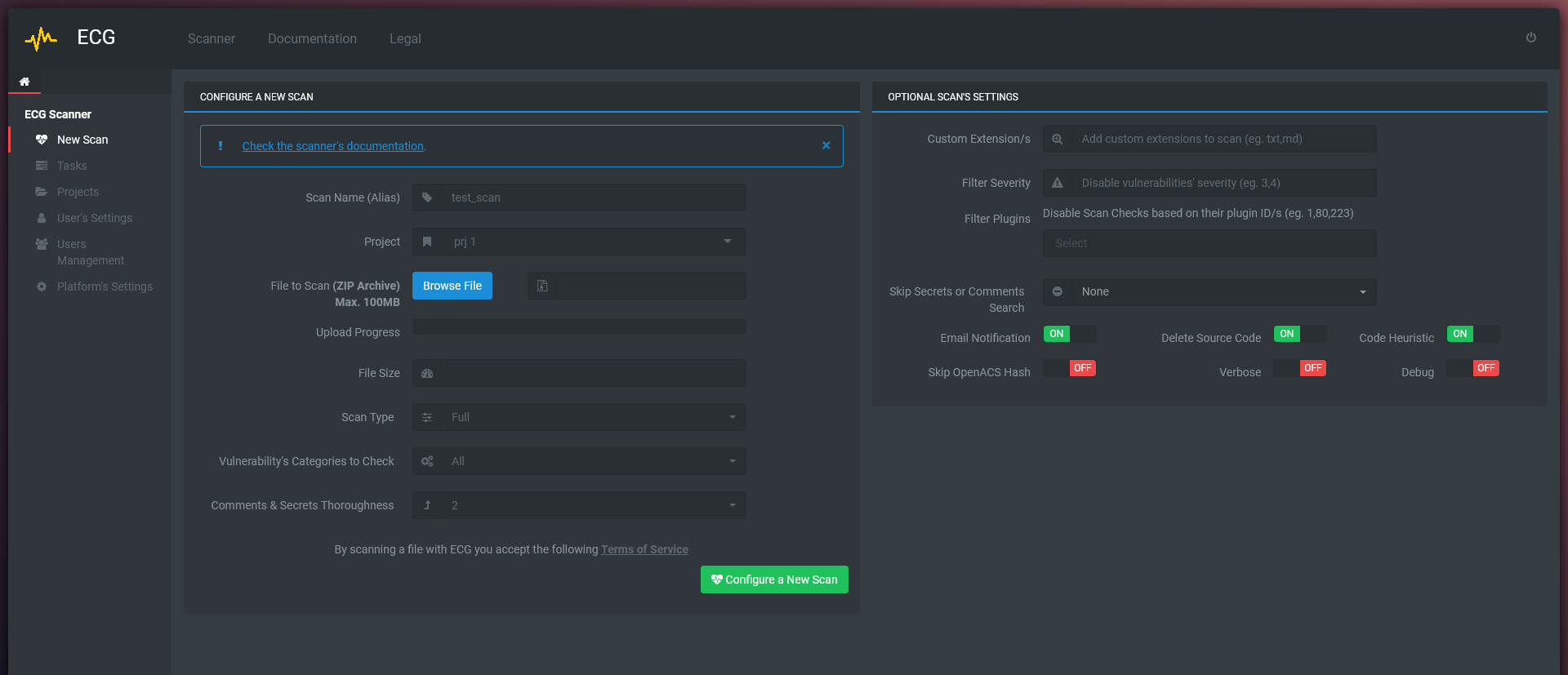
- On-Premises Deploy: Scan your code repository on your secure and highly-scalable offline appliance with a local ECG’s installation to comply with strict code privacy policies.
- API Support: Easily integrate ECG’s automated security testing into your continuous integration (CI/CD) and delivery tools. Manage your risks and detect vulnerabilities earlier in the development cycle before the code moves into production.
- Web UI: A new, fully refurbished Web UI that matches what’s under the hood. Fine-tune and customize ECG’s scan settings to tailor them according to your needs.
Table of Contents
ECG On-premises System Requirements
- Memory: 6-8 GB RAM
- Processors: 4 (2 processors 2 cores)
- Hard Disk: ~100 GB
ECG v2 Benchmarks
Average on 10x run (Full Scan, All Vulnerabilities, Scan Level 3, No Heuristic)
- Source Code: 204.6 MB
- Files to scan: ~12000
- LoC: ~5000000
- Execution Times:
- 0:24:49.704374
- 0:23:34.032893
- 0:22:07.914241
- 0:21:11.018293
- 0:21:43.177582
- 0:21:48.317756
- 0:22:38.845114
- 0:21:47.539437
- 0:22:23.411225
- 0:23:05.457007
- Average Execution Time: ~20m
- Average LoC/min: ~250000
- Average Files/min: ~600
 ECG Changelog
ECG Changelog
ECG v.2.1 (04/01/2021)
- Added: CVS Header on Report’s File
- Fixed: Erasing source code files now also delete original ZIP file
- Fixed: URLs Regular Expressions
- Minor bug fixing
ECG v.2.0 (30/11/2020)
- Introduced: Code Heuristics
- Added: Vulnerability Database
- Added: On-premises version
- Added: benchmarks
- Added: filters to scan (severity and disable specific plugins by ID)
- Added: “ad_returnredirect” vulnerability
- Added: CVE-2008-0553 vulnerability check
- Changed: UUIDv4 instead of timestamps to prevent collisions
- Changed: Now Procedure Calls, Procedure Definition and Packages ingore comment’s lines
- Fixed: URLs, IPS & Credit Card Regular Expressions
- Fixed: CLOC measurements
- Fixed: OpenACS Skip Hash message on verbose output
- Fixed: Procedure Calls, Procedure Definition and Package Regular Expressions
- Fixed: “do_uniq” for Procedure Calls, Procedure Definition and Packages
- Fixed: ACS variables
- Tested all the scanner options
- Refactored with general methods and classes
- Minor bug fixing
ECG v.1.1 (03/07/2019)
- Added: OpenACS database fingerprint! Now ECG will determine if any OpenACS file has been modified from it’s original version and it will only scan it if user’s modifications are detected. That will lead to improved scan time, lower false positives and meaningful results.
- Updated web interface: Documentation and Legal Tabs; file upload visual feedback
- Added: execution time to recap
- Fixed: CLOC and do_uniq function
- Fixed: ECG detection on “discard issues”
- Minor bug fixing
ECG v.1.0 (04/06/2019)
- Created a database of almost hundred check of dangerous function calls and vulnerabilities for: TCL/ADP language, Open ACS, AOLserver, NaviServer
- Added: Generate a list of procedures and sub-routines per file
- Added: Generate a list of parameters per file
- Added: Generate a list of imported packages
- Added: Scan for hard-coded secrets
- Added: Scan for comments
- Added: Export to CSV
- Minor bug fixing
ECG v.0.1 (30/03/2019)
- TCL and ADP code grepper
ECG’s Most Unique Features
- Unmatched Bug Detection: The first and the only solution able to detect real and complex security vulnerabilities in TCL/ADP source-code.
- Outstanding Performance: In-depth source code security analysis in minutes (instead of days) for continuous testing.
- Low False Positives: Highly-accurate analysis results to focus on meaningful findings without wasting time.
Our security experts are looking forward to helping you secure your TCL application with our leading code analysis technology: Contact Us.